Top Cybersecurity Threats in Healthcare 2022
The healthcare industry is facing a growing number of cybersecurity threats that are evolving in sophistication. According to Cisco, in 2021, the healthcare industry saw the highest Trojan activity compared to other industry sectors. The healthcare industry’s increasing adoption of mobile technologies, cloud computing, and Internet of Things (IoT) devices creates new opportunities for attackers to exploit both patients and personnel. Trojan activity and phishing make up 75% of malicious traffic in this industry. See graph below.

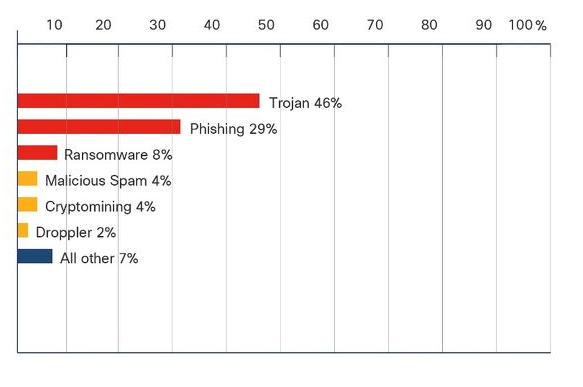
So, what is Trojan activity? Why is the most prevalent threat within the healthcare industry, and how can you protect yourself from it?
Whether you know it or not, Trojans are everywhere. In fact, they’re making millions of dollars for their developers and all without anyone knowing.
What Are Trojans?
A Trojan horse is a type of malware (malicious software) that appears as a legitimate program to trick users to install it. But once they download and install the program, the Trojan infects their system, and gives hackers access to everything on that computer (like personal or financial information). The name of this malware derives its name from Greek mythology — in the story, the Greek soldiers hid inside a big wooden horse and infiltrated Troy—similarly to how the malicious software pretends to be a legitimate program to infiltrate your system.
How Do Trojans Put Me at Risk?
Trojans are one of the most dangerous types of malware, and cybercriminals can use them for many different malicious purposes. They are extremely difficult to detect by users and are often missed by antivirus software.
There are dozens of different kinds of Trojans, and the damage they cause varies tremendously. Ransomware Trojans can encrypt your data so you can’t recover it, and other types of Trojans can steal your passwords, destroy or delete your files, or deactivate your antivirus and firewall programs. Trojans can also install keyloggers, which detect your keystrokes and can decipher your login information for online accounts.
Cybercriminals can also use Trojans to take over your computer and control it remotely to do their bidding. By doing so, the hackers can access all your files and accounts, steal your identity, or even use your computer to perform cyberattacks.
How Do Trojans Infect My Computer?
Trojans are programs that can infect your computer without you knowing it. Trojans can be disguised as free game downloads, websites, browser tools, or apps. Once you download the program, the Trojan gets installed and runs whenever your computer is turned on.
Trojans don’t spread on their own and typically require the user to download the false program. You can help prevent them from infecting your computer by never opening a file or downloading a program that you are unfamiliar with. Many malware-infected games also contain Trojans.
How Can I Protect My Devices from Trojans?
You’re not completely helpless, though. There are some things you can do to protect yourself from Trojans:
-
Never open an attachment or download a program unless you know exactly what it is and who/where it’s coming from.
This is a great general rule in terms of protecting yourself from a security breach, but this one is especially important when it comes to Trojan malware, since they require action on part of the user (you) to infect your computer.
-
Use antivirus software from a trusted company.
If you have an IT company managing your network, even better; they should already have installed antivirus software on all of your machines, however.
-
Keep your software up to date, including your operating system and your browser.
Keeping your software up to date is a great way to protect yourself from cybercriminals. Cybercriminals often identify vulnerabilities in software programs and exploit them to install malware. Software manufacturers frequently release updates that address these vulnerabilities, so it is essential you download the updates when available.
-
Use a firewall to help keep your internet connection secure.
The Internet is a great resource for everything from entertainment to work, but it also has its dangers. If you want to protect your personal information and keep your system safe from intrusion, you should use a firewall. These programs work by blocking unsolicited connections from other computers and can help prevent Trojans from entering your computer. Windows users have access to Windows Firewall, and macOS users have a built-in firewall as well, but you need to make sure it is turned on for extra protection.
The only way to be 100% safe from Trojans is to do nothing on the internet. Even then, if someone has access to your computer and knows what they’re doing, you may still be the victim of a Trojan attack. To use your PC with as much peace of mind as possible, make sure you have a reputable IT company, and follow the tips we laid out. The security precautions listed above may not guarantee that you won’t be infected by a Trojan, but they’ll help reduce your risk considerably.
